We all know Bitcoin, which is arguably the most popular cryptocurrency based on a blockchain. Bitcoin maintains its security through Proof-of-Work (PoW), which relies on solving useless computational puzzles using massive amount of resource (i.e., electricity). The annual energy consumption of Bitcoin is even comparable to the annual electricity bill of Norway. Proof-of-Stake (PoS) blockchains such as Ethereum avoid such electricity waste in PoW. But PoS comes with another inherent resource waste: It requires locking up a huge amount of capital, leading to a large opportunity cost for the cryptoassets. For example, at any point of time in the year of 2024, more than 20% of the total Ethereum stake is locked.
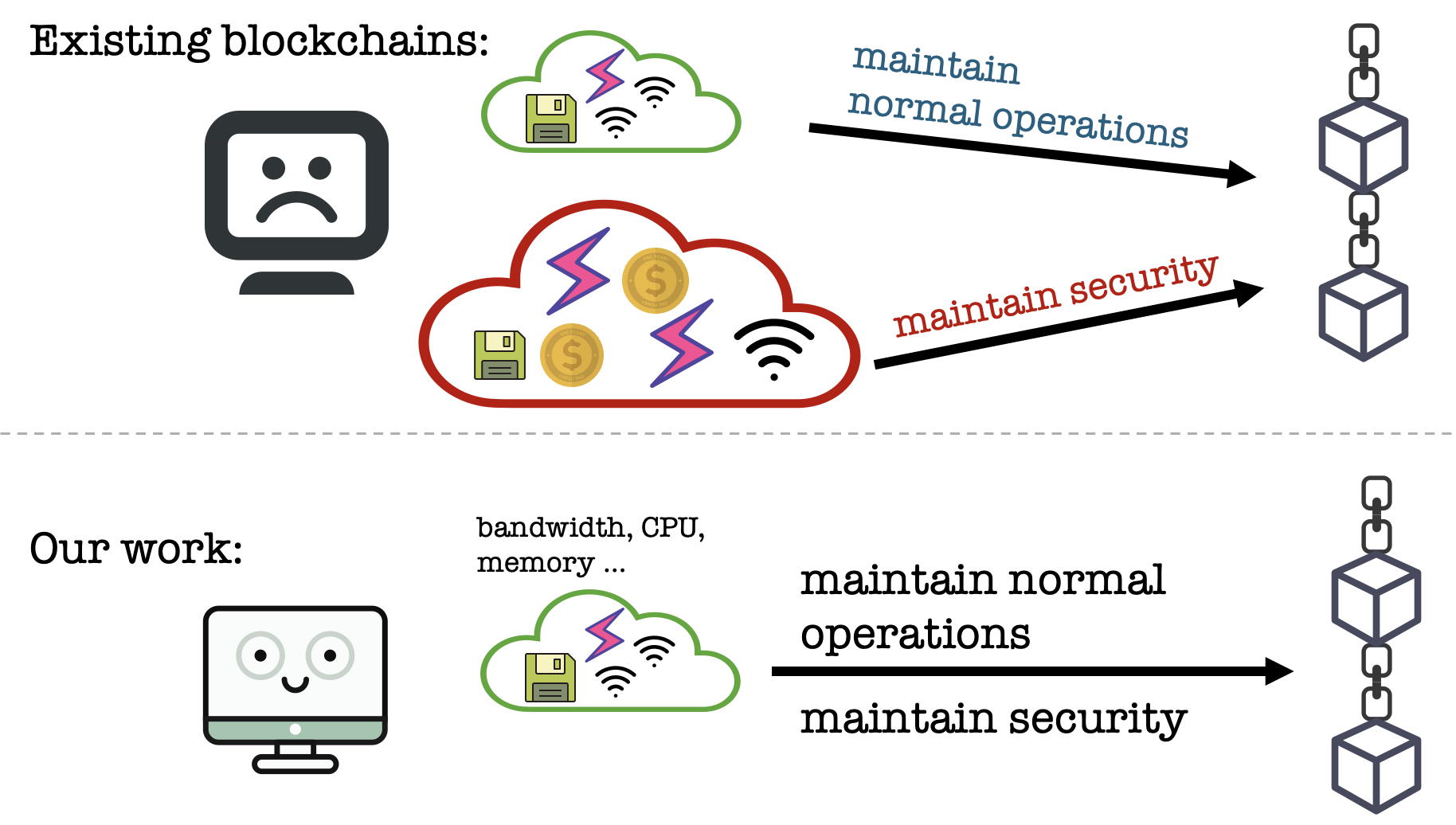
Blockchains burn such resources, in order to provide the desired security guarantees. But we observe that even if security is not a concern, for a blockchain just to deliver its basic functionality as a distributed ledger, the blockchain already needs to consume various resources. These resources include CPU cycles (to perform necessary blockchain computation), storage space (to store the blockchain itself), and bandwidth (to exchange blockchain messages). We call such resource consumption in-protocol resource consumption. This then leads to a natural yet intriguing question:
Can we simply piggyback on in-protocol resource consumption, to achieve the desired security guarantees?
A positive answer would enable blockchains to avoid wasting resources, at a fundamental level.
Our work gives a positive answer to the above question. Specifically, we focus on bandwidth, a resource that is heavily utilized in high-throughput blockchains. Our basic idea is that honest nodes in a high-throughput blockchain are already consuming a large amount of bandwidth. Hence if an attacker tries to create many fake nodes to sabotage the blockchain, in order for the fake nodes to look real, the attacker has to consume a large amount of bandwdith for each of the fake node, which is prohibitively expensive.
Driven by this intuition, we have designed a novel blockchain that can exploit in-protocol bandwidth consumption to achieve the desired security guarantees. Nodes simply observe each other's bandwidth consumption during normal operation, and our design can then use such information to make the blockchain secure.
More technical details can be found in: